The Evolution of Computer Hackers: From Heroes to Outlaws
A documentary on the origins of computer hackers and their impact on society.
00:00:00 A documentary on the origins of computer hackers reveals how they started a revolution in the world of computers, becoming heroes before being labeled outlaws.
🏴☠️ Hackers initiated a revolution in the computer world and were once considered heroes.
📞 Phone networks played a significant role in the development of hacking techniques.
🔒 Manipulating phone systems led to free long-distance calls and a technological challenge.
00:06:43 The documentary explores the early days of hackers and their ability to manipulate phone systems. It delves into their expertise in social engineering and the fear of intrusion in telecommunication.
📞 Telephony companies' easily accessible system and the success of the blue box technology intrigued hackers.
🕵️ Hackers became experts in manipulating both the mechanical aspects and employees of telecommunication companies.
🔐 The manipulation of telecommunication systems caused paranoia among the public about the invasion of privacy.
00:13:27 The video explores the origins of computer hackers and their impact on the technological revolution, focusing on key figures like the Captain Crunch and Steve Wozniak. It highlights their exploration of telephone networks and the creation of personal computers.
🔑 The hacker revolution was sparked by the creation of personal computers, inspired by the exploration of telephone networks.
💻 Early hackers like the Captain Crunch and Steve Wozniak were pioneers in using technological loopholes to manipulate systems and make unauthorized phone calls.
🌐 The emergence of the Homebrew Computer Club in the 1970s marked a significant milestone in the development of personal computers and hacker culture.
00:20:12 A documentary about the history of computer hackers, their fascination with technology, and their contributions to the development of personal computers.
📦 Steve Wozniak fascinated his peers with a network inside a box in the garage, sparking interest in computers.
🔧 Home computer enthusiasts formed a club to share information and solve problems, pushing the boundaries of technology.
💻 The club members experimented with hardware and software, creating games, music, and graphics, leading to groundbreaking advancements.
00:26:56 The rise and fall of the Home Computer Club and the impact of hackers on the computer industry.
📅 The home computer club era replaced by serious businesses like Apple, leading to the end of the club.
🚫 Hackers were no longer welcome in the new world of computer business.
⏰ Kevin Mitnick became a prominent hacker, but his arrest marked a turning point in public perception of hackers.
00:33:41 The documentary discusses the evolution of hackers and their transition from being considered hobbyists to criminals in the world of computer hacking.
🔒 The advent of the internet eliminated the boundaries for hackers, making it difficult to secure information.
⚖️ Piracy transformed from a hobby to a criminal offense, leading to the need for new laws and technology to combat cybercrimes.
🚫⌨️ Kevin Mitnick, a notorious hacker, evaded the FBI multiple times, showcasing his expertise in hacking and his determination to stay ahead of the law.
00:40:25 A documentary about the early history of computer hackers and their impact on society. Kevin Mitnick was falsely accused and eventually convicted, highlighting the changing morality of hacking.
💻 The rise of hacking in the early days of the internet and the growing concern for cybersecurity.
🔒 The importance of secure systems to protect sensitive information and prevent unauthorized access.
🔑 The story of Kevin Mitnick, a notorious hacker, and his legal battles surrounding fraud and software piracy.
You might also like...
Read more on Science & Technology
AI Integration in 60 Minutes: An Actionable Masterclass
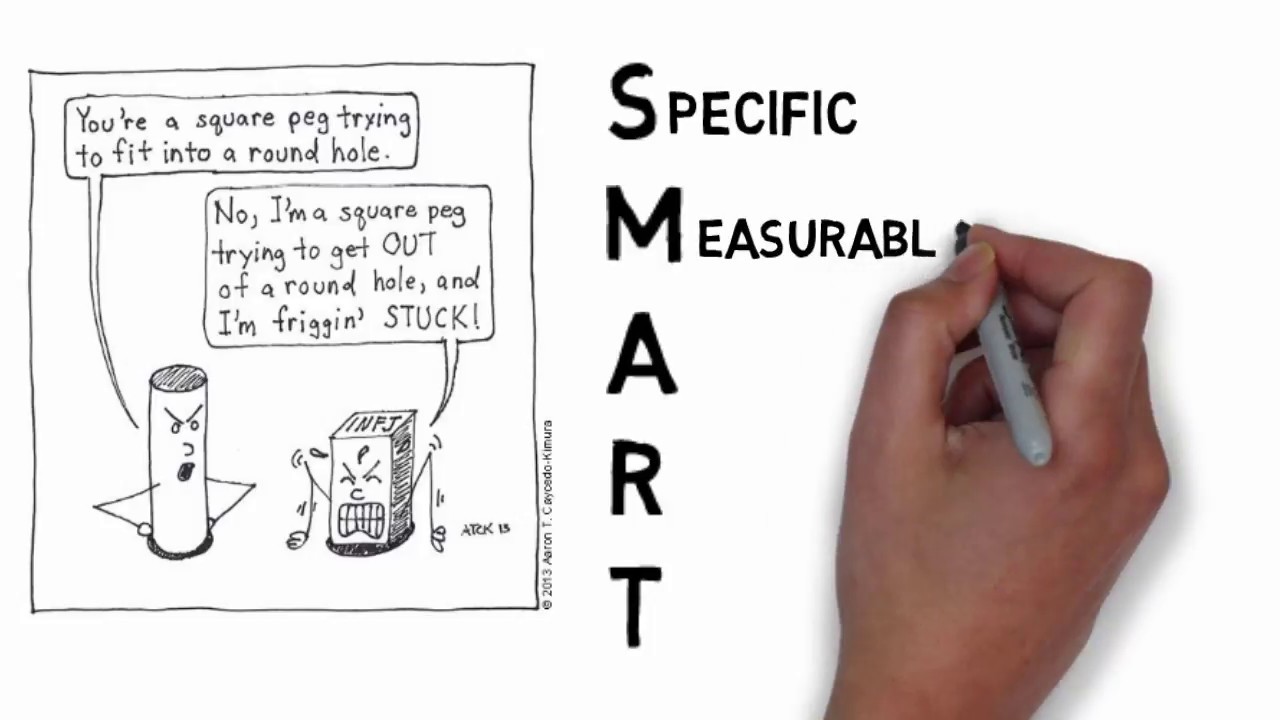
SMART Goals - Quick Overview
Capitulo 63 - Guyton
![Los MÓVILES con MEJOR CÁMARA del 2024 | Los 5 Teléfonos con mejor cámara [2024]](https://i.ytimg.com/vi/B4enh1LRCkk/maxresdefault.jpg)
Los MÓVILES con MEJOR CÁMARA del 2024 | Los 5 Teléfonos con mejor cámara [2024]

ComfyUI : Ultimate Upscaler - Upscale any image from Stable Diffusion, MidJourney, or photo!

Immigration and migration in the Gilded Age | Period 6: 1865-1898 | AP US History | Khan Academy